Phishing
OH NO!
You've been phished!
What is remote work opportunity phishing?
What is phishing?
- A psychological attack used by cyber criminals to trick you into giving up information or taking an action.
- These attacks often begin with a message pretending to be from someone or something you know.
The internet and its connected devices are constantly changing and multiplying and
cybercriminals have become crafty in luring users giving up their personal information.
Emails and other types of instant messages can be generated to look like legitimate
messages coming from a trusted source, such as an important work-related action (such
as an invoice, account update, or other urgent notice requiring credentials).
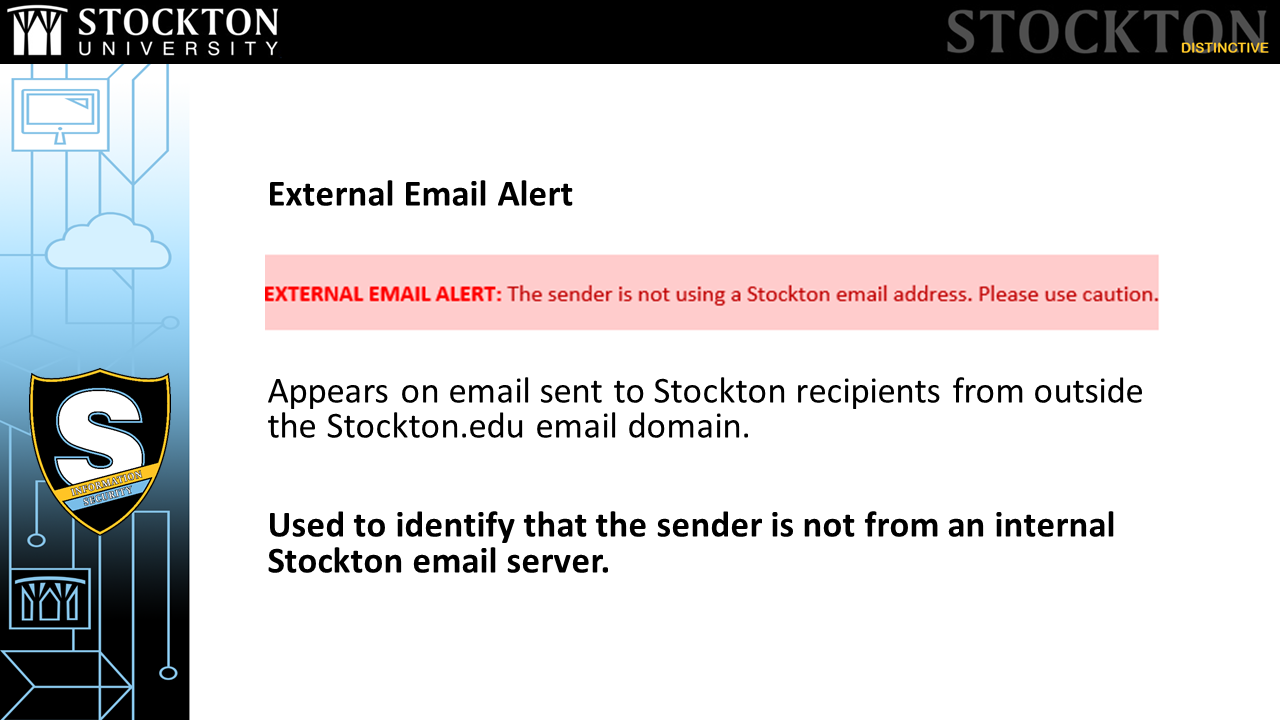
External Email Alert
- A highly-visible banner placed at the beginning of all email sent to Stockton employee email accounts from outside the Stockton.edu domain
- Used to identify that the sender is not from an internal Stockton email server
- Students see a similar warning for unfamiliar or external contacts
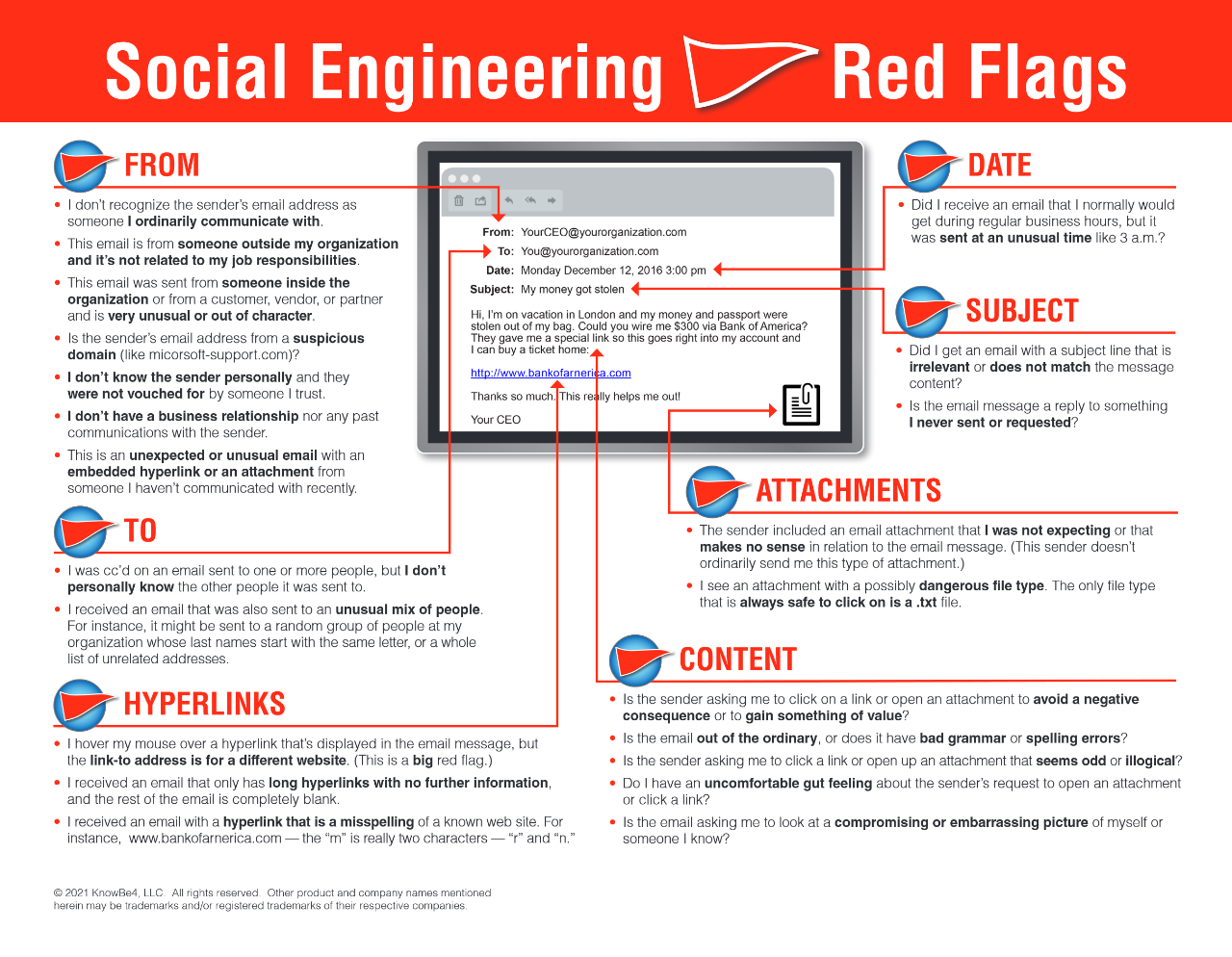
Examples of Phishing
Email is the most common method used to phish unwary users of their information. The easiest way to tell a legitimate email from a phish is by looking for these tell-tale red flags:
Avoid Being a Victim
- Be aware of suspicious messages. Check carefully for telltale signs of phishing and always remain skeptical of anything found online.
- Keep your computer's operating system and anti-virus software up to date.
- Forward any suspicious emails found in your inbox to phishing@stockton.edu.
- Stockton employees: use Outlook to block spammers and phishers.
- In Outlook (client version), right click on the suspicious e-mail, select Junk and click on "Block Sender."
- In Outlook Web App (web version), right click on the e-mail and click on "Mark as Junk."
- Stockton students: learn how to block unwanted messages in Gmail.
- Visit www.onguardonline.gov to learn more about ways to prevent phishing.